27k1 ISMS Product Information
The 27k1 ISMS product has been designed and developed in accordance with the ISO 27001 standard by Information Security professionals and ISO 27001 practitioners. This software provides a total solution for ensuring compliance and achieving ISO 27001 certification while maintaining the ISMS through management meetings, actions and continuous improvements.
The 27k1 ISMS software is comprised of the following, integrated system modules. Each module description links to a short video, providing greater detail.

Getting Started
This module enables the user to set the guidelines for how the 27k1 ISMS assesses risks, threats and vulnerabilities to Information Security assets.
Here the scope of the ISMS is submitted along with those information Security assets and objectives that are covered by the scope.

GAP Analysis
The Gap Analysis module allows users to assess and allocate each Security Control and Clause effectively and work to ensure their implementation.
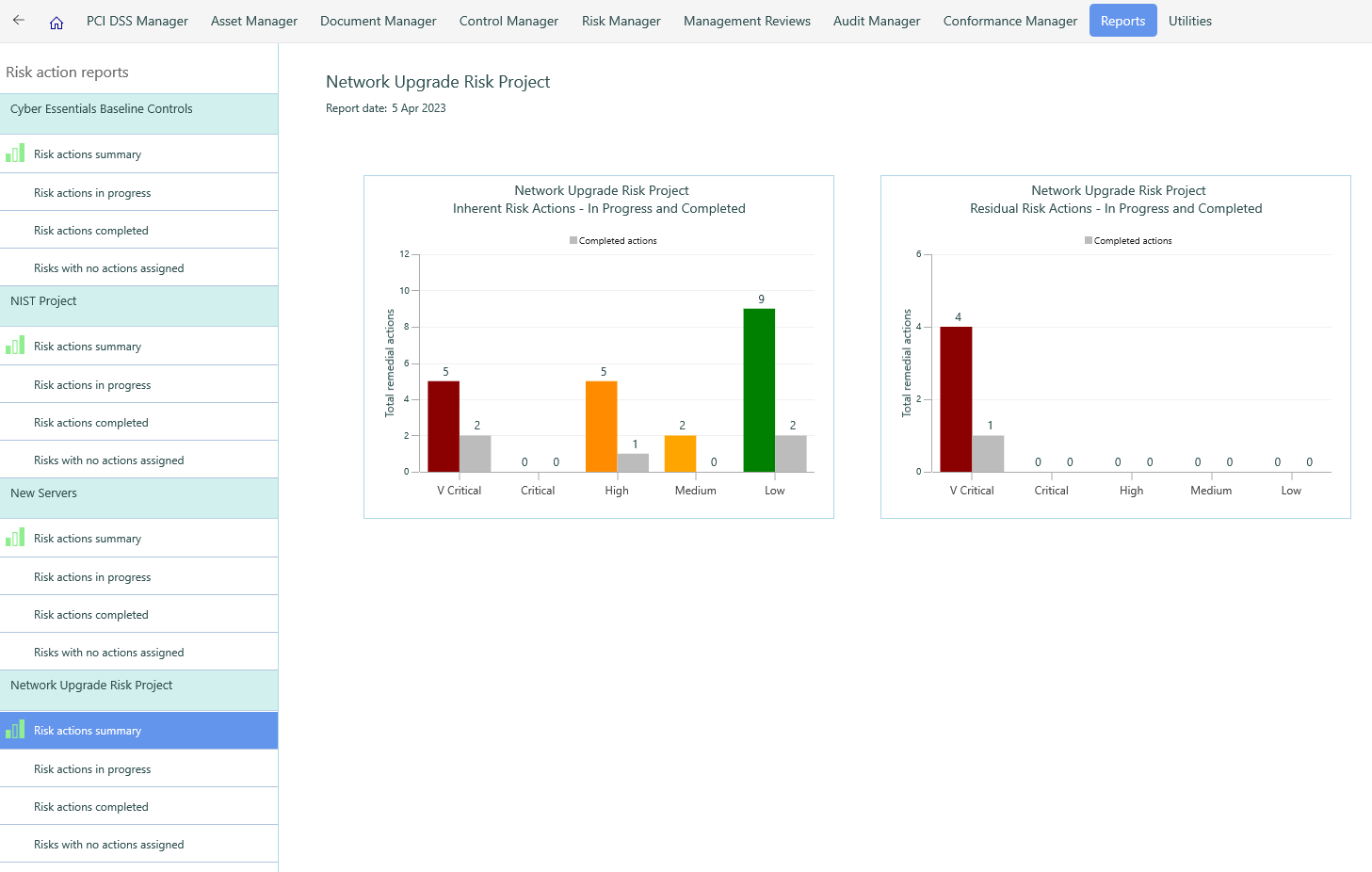
Gap Analysis Reports include Actions, Progress and Summary Reports so that the business can review its efforts to assess and reduce the risks to its Information Security position.

ISMS Manager
This module allows the system user to set the information security policies, risk parameters and weight the impact and outcome of a risk assessment.
The process is logical, intuitive and can be configured at every stage.

Asset Manager
All Information Security assets are managed within the Asset Manager, including personnel, hardware, software, outsourced services, etc.
Each asset type is individually managed according to the ISO 27001: 2013 standard.
Those companies that do not have an Asset Register or HR Register can choose to adopt or cross reference the system’s functionality, since it delivers these additional benefits.

Document Manager
The 27k1 ISMS accesses your own documents through URL’s or hyperlinks.
This means that you can continue to use, create and access your own company’s Document Management solution, rather than duplicate a system or pay for an expensive DMS that you may not need.

Control Manager
All Annex A Controls are listed, each being subject to user selection in readiness for automatically producing a Statement of Applicability. Here, the user can assign documents to each Control and manage the actions that have been assigned.
The Statement of Applicability may be created in draft format within the Control Manager at any time, then formally issued when all the Controls and supporting documents are in place.

Risk Manager
This key module draws upon the guidelines set in the Getting Started module. It offers a comprehensive and flexible, risk based scenario valuation, assessment and treatment solution.
The system provides numerous examples of threats and vulnerabilities, allowing the user to choose those that may apply to an Information Security asset risk assessment and consider the impact and actions that may follow.

Conformance Manager
From the integrated Management Reviews and Meetings, security breaches may be identified, allowing nonconformances and corrective actions to be raised, tracked and resolved.
Conformance Reports highlight severity, root cause and preventive measures to be applied. These are tracked through start, progress and closure dates as well as allocating resources responsible for each action. In this way, the 27k1 ISMS reports on progress towards ISO 27001 compliance.

Review Meetings
Using Microsoft Office 365 functionality, the system allows meetings to be diarised, invitations sent, agendas are set and meeting notes recorded.
Review meetings allow nonconformances and actions to be raised, tracked and resolved, enabling the continuous improvement of the ISMS.
Internal Audits
The Audit Manager is a complete audit workflow system: from raising audit plans with their related activities, through to assigning audits to auditees, raising questions, recording nonconformances and presenting the findings through management reports.
Reports