PCI DSS v4.0 Compliance Software
ISO 27001:2022 ISMS Software
27k1 ROC Management System (RMS)
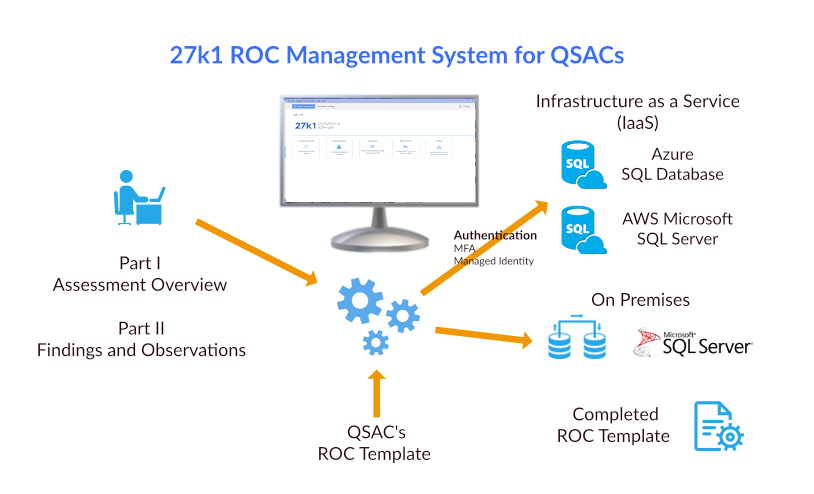
The 27k1 ROC Management System (RMS) has been developed for certified QSA companies, wishing to complete the Report On Compliance for Level 1 clients.
The perfect solution for certified QSAs, streamlining the ROC assessment process, cutting costs, improving accuracy and generating efficiencies.
Load your own, corporate branded ROC template into the software to produce corporate branded assessments
Create your "Response Library" to automate responses for every ROC assessment
Use MFA or Managed Identity to control and secure QSA access to the 27k1 RMS
Manage QSA and QA access to each ROC assessment using their account name
Segment Documentation, Interview, Observation and System evidence requirements to improve workflow
Improve QSA efficiency and reduce stress - saves around six days per ROC Assessment
27k1 RMS System Training – Free of Charge
QSA Company Reference

Evolution Global Security is an award winning, QSA Company with offices in the UK, Channel Islands and Hong Kong. The business delivers a full range of PCI DSS services across the card processor, retail, insurance and financial sectors, including v4.0 ROC assessments.
Evolution recently started to use the 27k1 ROC Management System and this is what their Managing Director had to say:
“The 27k1 PCI DSS auditing tool offers a comprehensive and user-friendly solution for managing our PCI DSS compliance. Its intuitive interface has made the auditing process seamless and efficient”
27k1 ISMS Software
ISO 27001:2022 contains 93 Annex A security controls and changes to several ISMS clauses which are supported by the 27k1 ISMS.
The Annex A controls span 4 main themes:
1. Organisational controls (37 controls)
2. People controls (8 controls)
3. Physical controls (14 controls)
4. Technological controls (34 controls)
The 93 controls include 12 new controls that have been added in response to major shifts in both technology and threats since 2013. The emphasis of the control changes is on cyber-attack prevention, detection and response, as well as better protecting sensitive data.
Those using spreadsheets to manage their ISMS data face a huge challenge in mapping the 2013 controls across to the 2022 controls.
The 27k1 ISMS software allows easy transition from the 2013 Annex A Control set to the 2022 Annex A Control set for those companies that have achieved ISO 27001 certification.
The software provides gap analysis, risk management, full control of management review meetings, internal audits and nonconformities with dashboard style reporting.
A selection of clients using the 27k1 ISMS software
27k1 ISMS for Information Security Specialists
Implementers & Auditors
This software is a key system for your company's implementers and internal auditors. It allows you to move away from unwieldy and complex spreadsheets to a clear and easy to use system.
Used on an ongoing basis, the 27k1 ISMS can be readily referenced in the board room and prepares you for future audits at any time.
ISO27001 Consultants
Please contact us to discover the opportunities available to limited companies by partnering with us.
Testimonials
The 27k1 ISMS is the perfect ISO 27001 solution for all businesses
The 27k1 ISMS application:

GAP Analyses
Carry out a GAP Analysis using preconfigured ISO 27001 controls and clauses which suggest the recommended documentation.
Update GAP actions or tasks using the detailed project reports to track their progress.

ISMS Framework

Asset Management
All Information Security assets are managed in the Asset Manager, including personnel, hardware, software, outsourced services, etc.
Companies using spreadsheets or do not have an Asset or HR Register can choose to adopt the system’s asset management functionality, since it manages all asset details including the asset's lifecycle.

Documentation

ISO Controls & SoA
All Annex A Controls are listed, each being subject to user selection in readiness for automatically producing a Statement of Applicability. Assign documents to each Control and manage the actions that have been assigned, demonstrating compliance and on-going improvements.
SoA’s are offered in draft format then formally issued when all the Controls and supporting documents are in place.

Nonconformities

Review Meetings

Internal Audits
The Internal Audit Manager module pulls in data that has been submitted to the 27k1 ISMS. It enables comprehensive internal audits on Clauses, Controls, Processes, Locations, Departments and Suppliers.
The system allows questions to be raised, audits to be planned in detail with auditees to be assigned and scheduled. The audits facilitate the raising of nonconformances, implementation of corrective actions and on-going improvements to the company’s information security position.
Reports
The 27k1 ISMS Platform
Retain Control of the ISMS
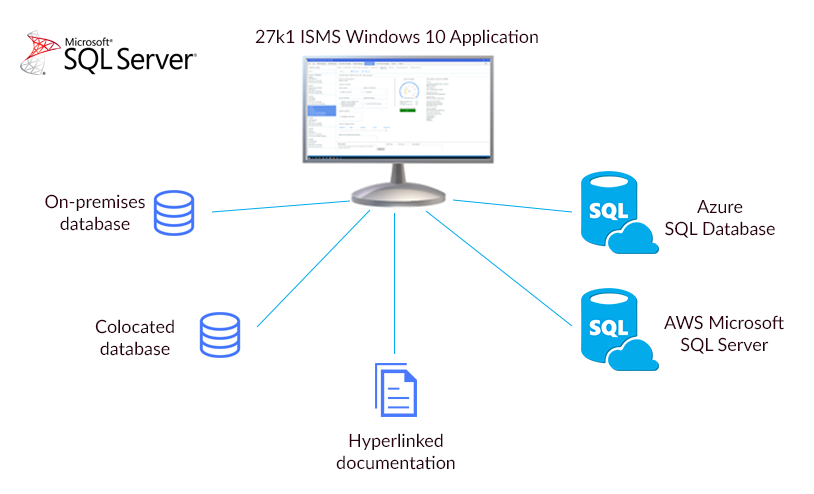
Your company retains control over and access to its’ ISMS data at all times.
All ISO 27001 ISMS and PCI DSS data is stored on Azure SQL Database, Amazon Microsoft SQL Server Database or a Microsoft SQL Server database located within your company network.
All documents, images, supporting evidence and certificates are stored, accessed and amended on your own document management system or Intranet using hyperlinks.









